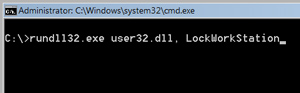
Step 1 – Open a DOS promot for launching a special command line. One simple way you can do it would be by clicking Start/Run, typing CMD.
Step 2 – Enter the command line for locking your station:
rundll32.exe user32.dll, LockWorkStation
and your computer will be locked.
The computer lock can be achieved in many ways, here is bellow an example which is using the native screen saver possibilities. For a more professional option check the 14 days trial of the usb lock software and folder lock software.
Bellow you find the procedure for installing a password-protected screen saver. Please make sure you have selected a screensaver and it is set to start within 15 minutes of inactivity. (more…)
If you don’t have a keyboard with a Window key or simply don’t like the keyboard method, then here’s how you can make a desktop shortcut to lock your computer. Bellow are the instructions used to lock down your computer using a shortcut. (more…)
 You can use Group Policies to lock down a Terminal Server session on a Microsoft Windows Server 2008-based or Microsoft Windows 2000-based computer. With the following settings, even the administrator account will have restricted access. It is highly recommended that you create a new organizational unit instead of modifying the policies on an existing one.
You can use Group Policies to lock down a Terminal Server session on a Microsoft Windows Server 2008-based or Microsoft Windows 2000-based computer. With the following settings, even the administrator account will have restricted access. It is highly recommended that you create a new organizational unit instead of modifying the policies on an existing one.
Note: The use of these policies does not guarantee a secure computer, and you should use them only as a guideline. ID Security Suite offers you also a usb lock, device lock and folder lock solution.
The Dsacls.exe tool
Dsacls.exe is a command-line tool that you can use to query the security attributes and to change permissions and security attributes of Active Directory objects. It is the command-line equivalent of the Security tab in the Windows Active Directory snap-in tools such as Active Directory Users and Computers and Active Directory Sites and Services. You can use Dsacls.exe to lock out Terminal Services end-users from files and folders on a Windows Server 2003-based computer or a Microsoft Windows 2000-based computer.
Check also the article: How to use Dsacls.exe in Windows Server 2003 and Windows 2000 and the attached PDF document to this post.
ID USB Lock Key is a security program meant to protect your computer from unauthorized users. It denies access, by providing a security block-screen which can be unblocked with the USB stick where you have the key generated by the program. You can download a 14 days trial version or you can get your hands on license on the safe order page. (more…)
Pop-ups are an extra window which opens on your computer screen without asking you. We’ve all seen them on our screens. They can be quite annoying and many people frown on them as a form of spam. Pop-ups have become quite prolific on the internet, ranging from being a minor annoyance to being a major annoyance. There are several reasons why a pop-up is used, advertising being the most common. The best way to block pop-ups is to use a pop-up stopper like ID AntiPopup. (more…)
As people spend more and more time online, the risk of getting a virus increases. It happens to all of us at some point in time. If you are not able to detect viruses and remove viruses immediately, your computer system could come crashing down. That’ why you need to use a good anti virus software program, like Eset Nod32 to keep your computer virus free. (more…)
In today’s high tech world it seems anything we want is only a keystroke away.
Sadly this is the same for the crooks out there. Every time you use your computer you leave files behind that can be stolen by a hacker. Often, these files will contain personal information. To protect privacy and stay secure, you will need to use a trace washer, which will erase traces of all your internet activity. (more…)
Browser hijacked, strange pop-ups appearing for no reason? Is your computer running really slow? It’s time you knew how to protect yourself!
These days, the adware threat to your computer, is no laughing matter. Not only is it annoying, it can create havoc with your system, and jeopardize your personal information. That is why it is so important to detect adware, and remove adware as soon as possible. (more…)
Securing your digital life takes on a new level of importance. Most people would rather lose their phone line than their email service; this explosion of email has comes a parallel rise in email-based threats. This threats range from minor nuisance to major resource drains and create serious vulnerabilities. No computer user can afford to ignore the problem. Spam, viruses, worms, phishing, blended threats and inappropriate use of email; they are all part of the same issue: content security. (more…)
 The
The